Kali Purple SOC: Part 7 – Installing OPNsense Integration in Kibana and Filebeat in Byzantium

Installing Kibana OPNsense Integration
Open the Elastic dashboard, click Fleet.
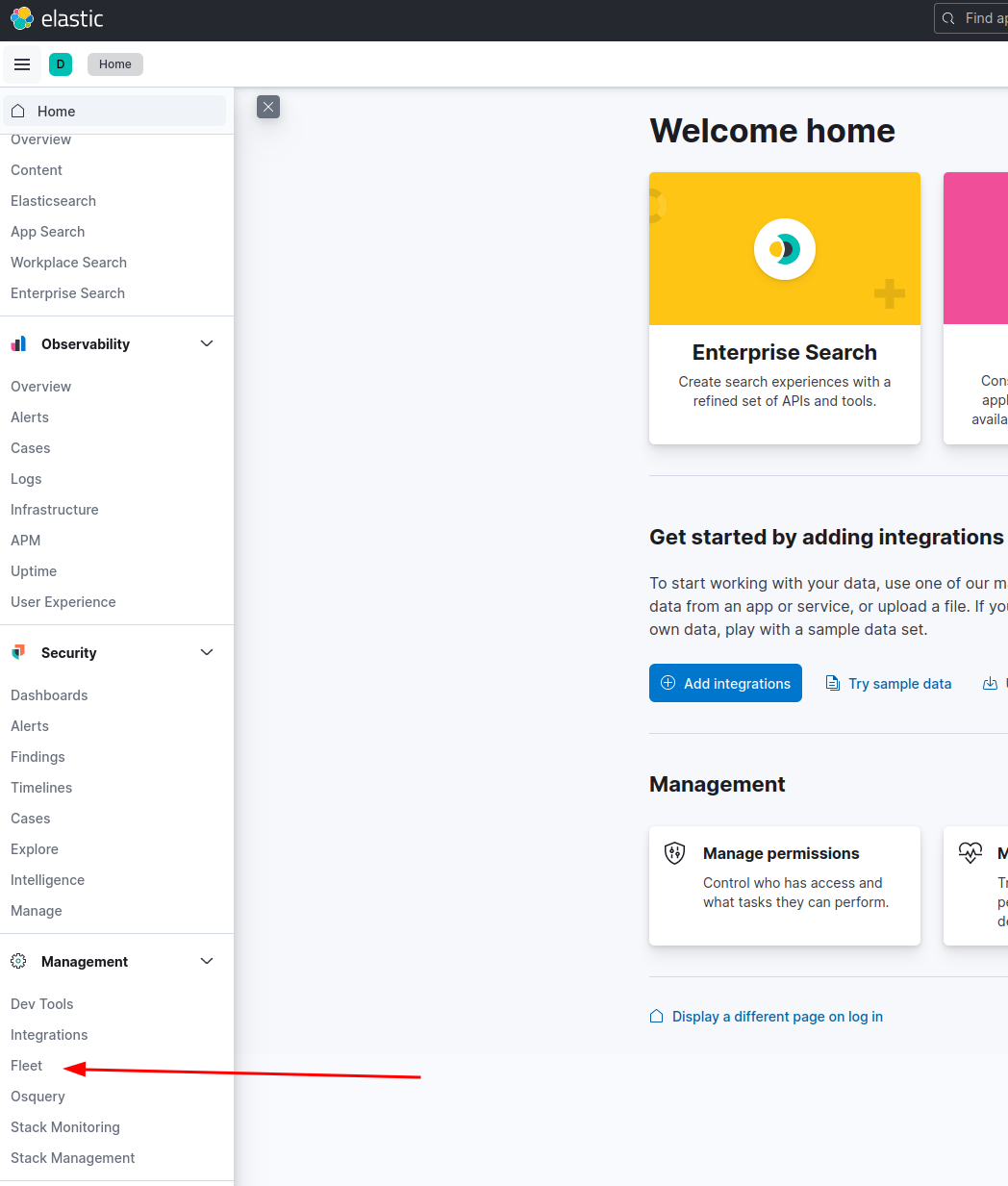
Follow the screenshots below:
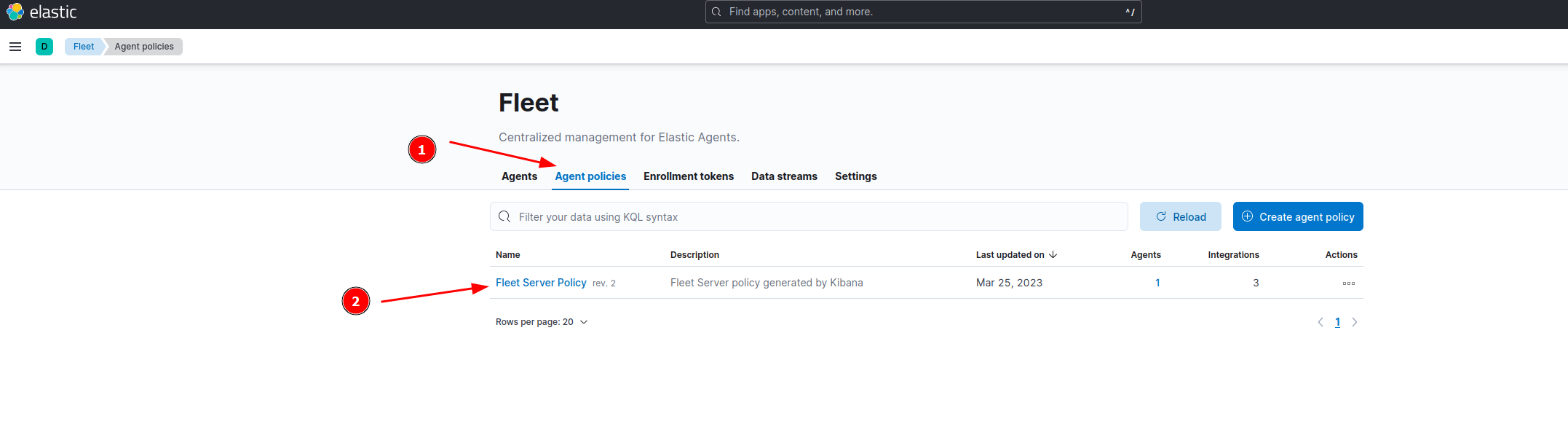
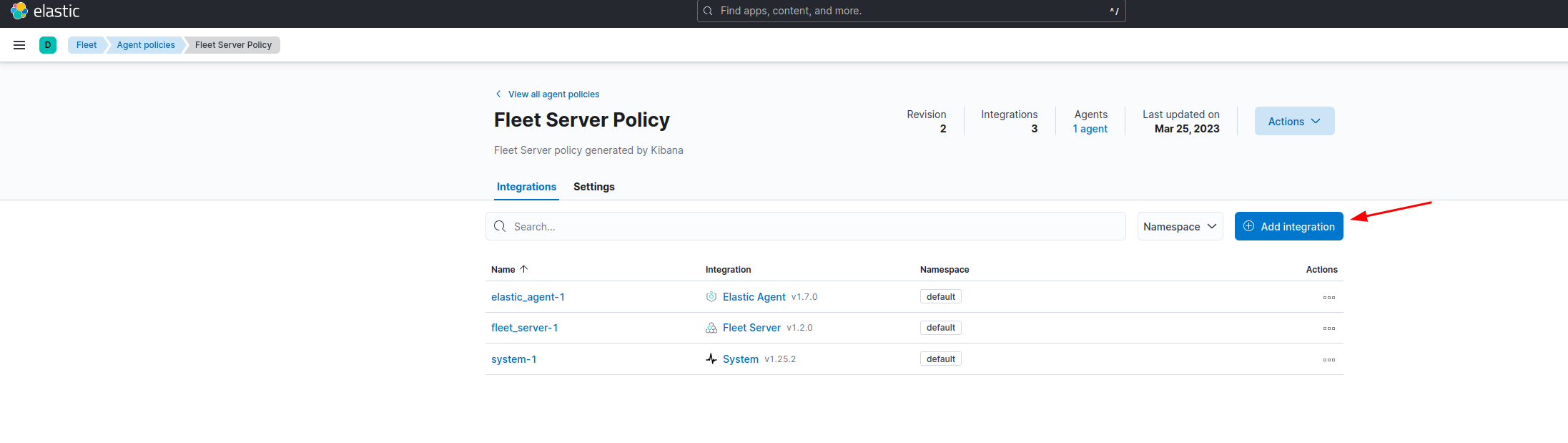
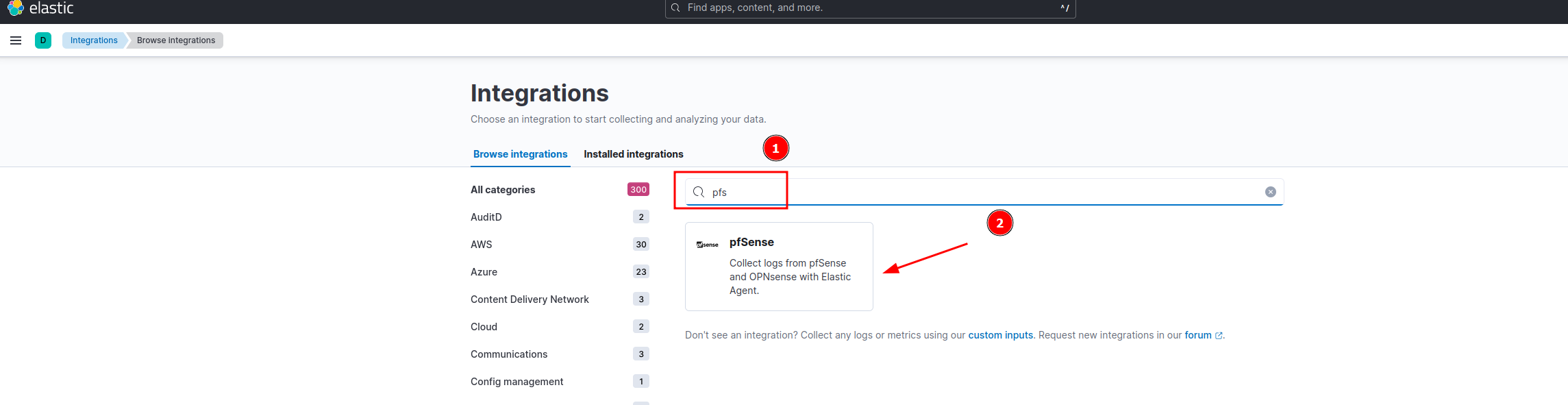
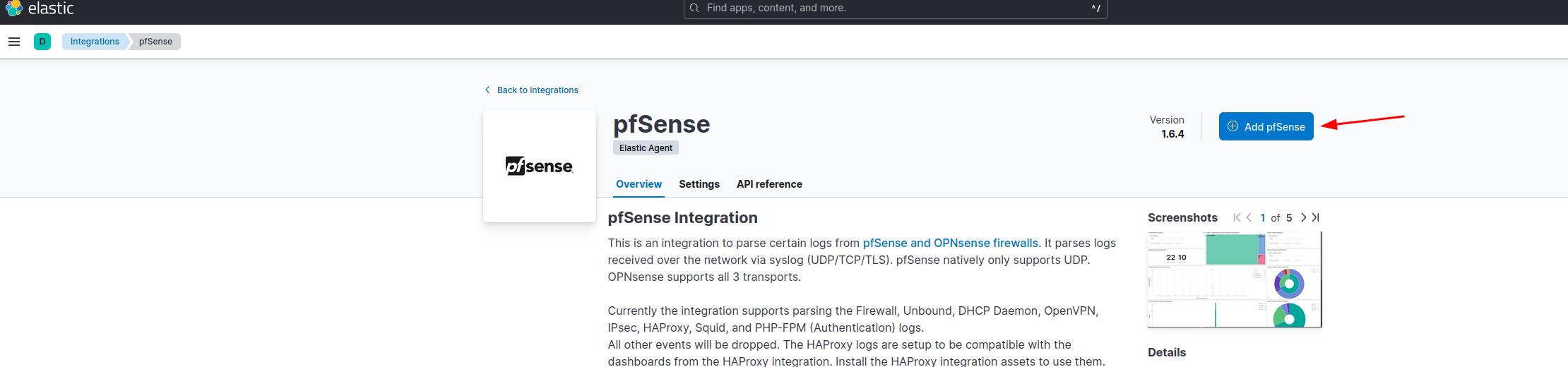
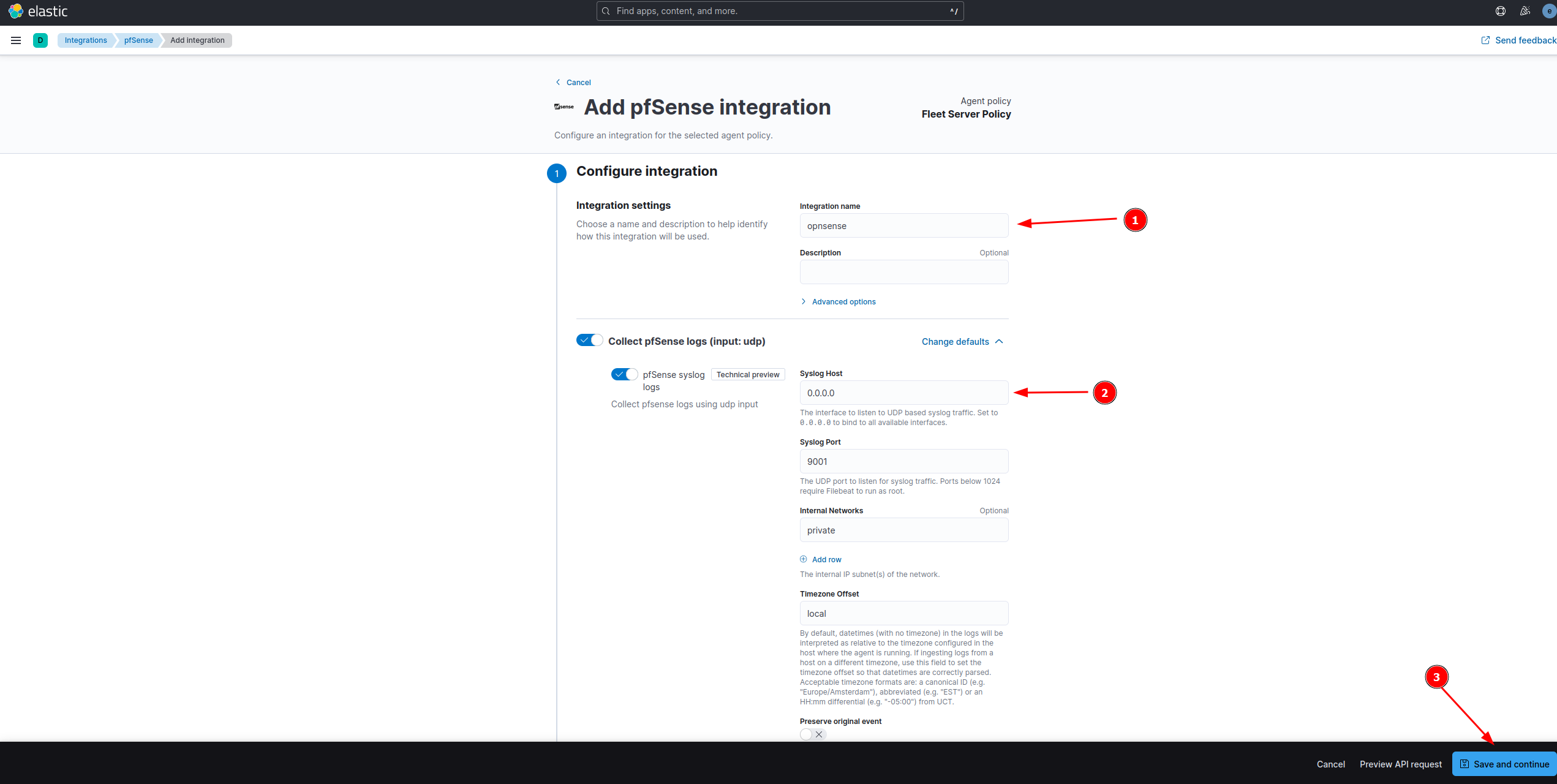
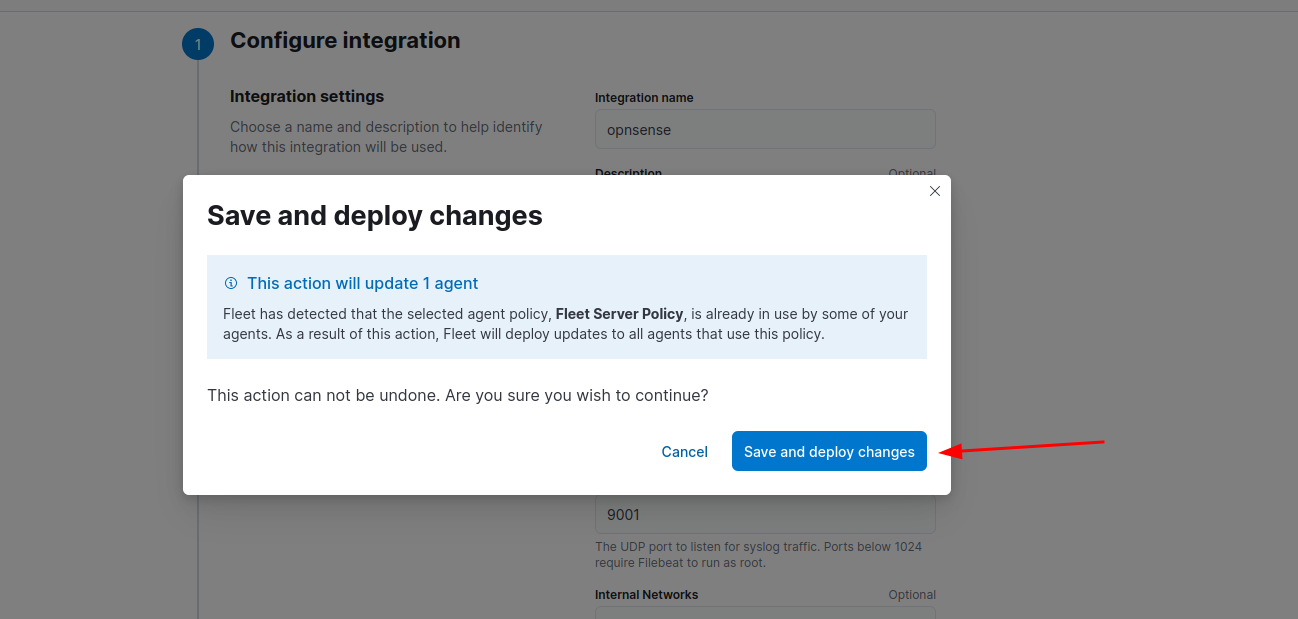
Should look like the screenshot below:
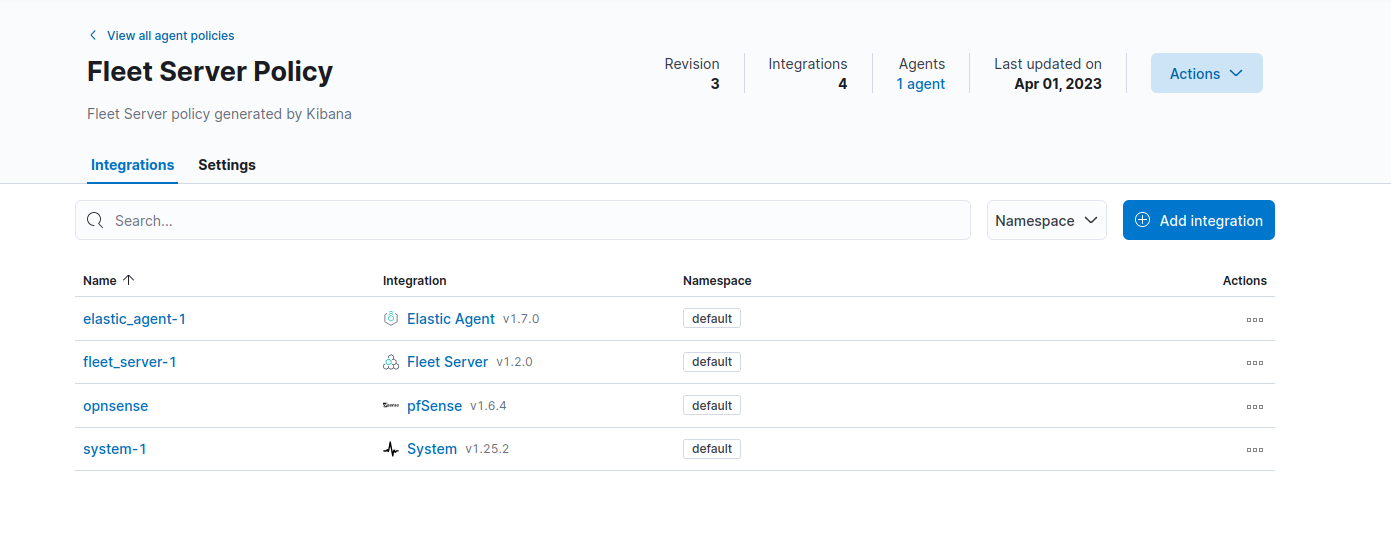
Configure OPNsense to send logs to Kali Purple
Follow the screenshots below:
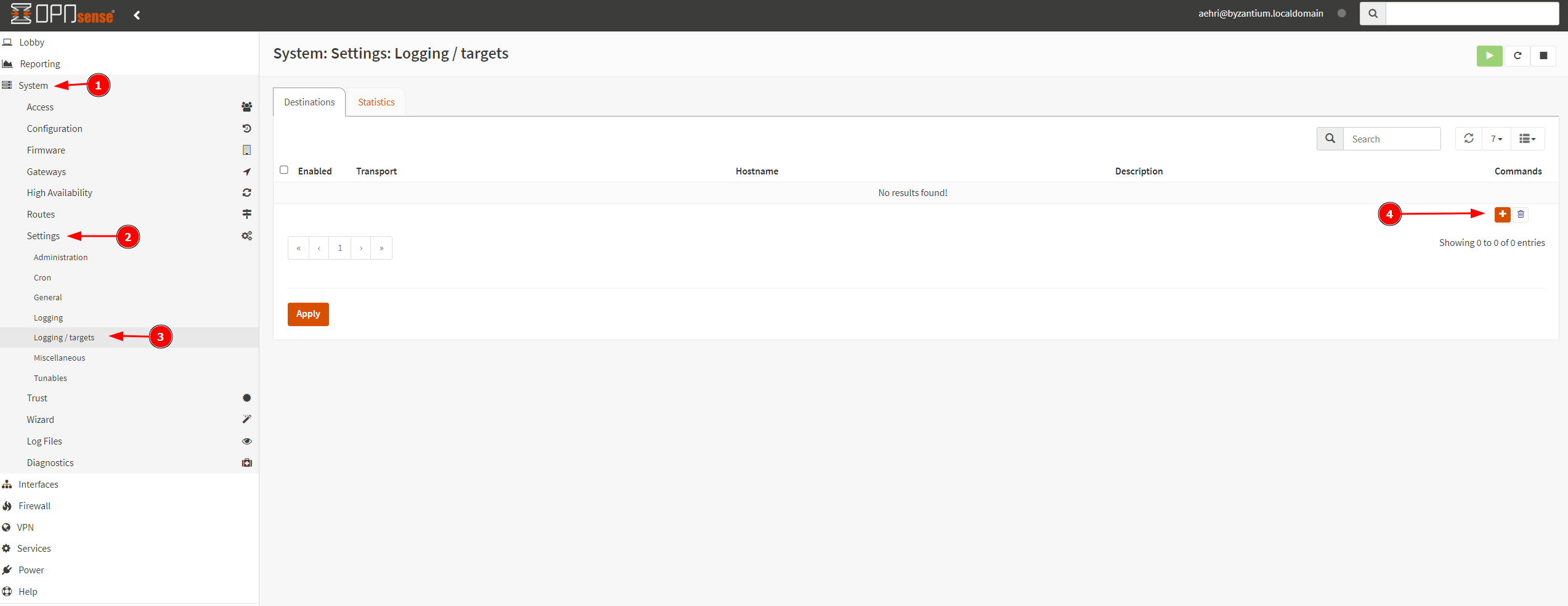
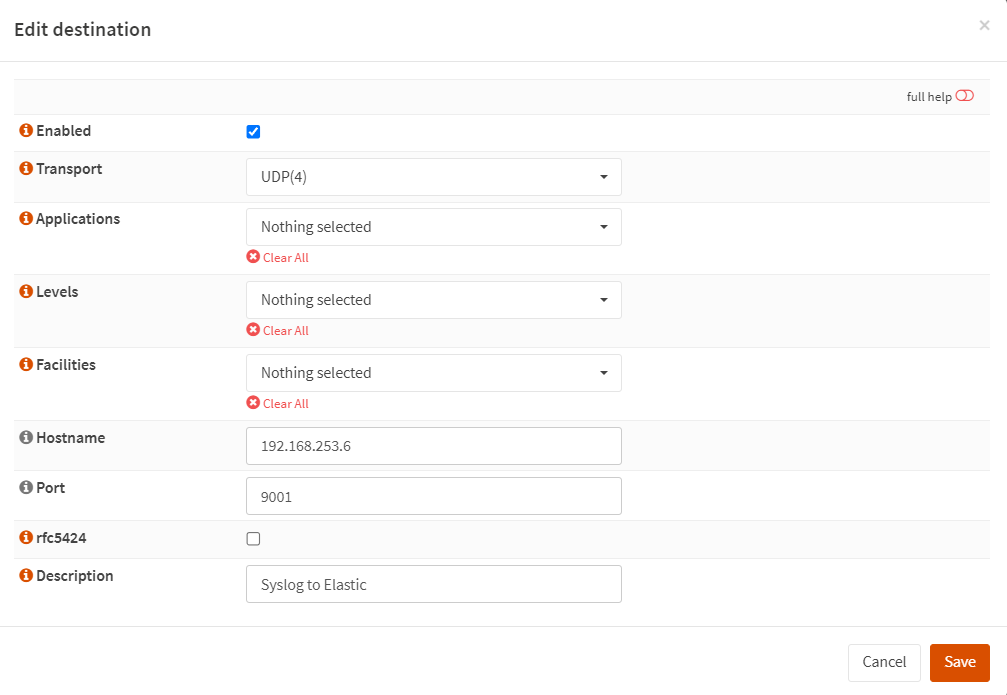
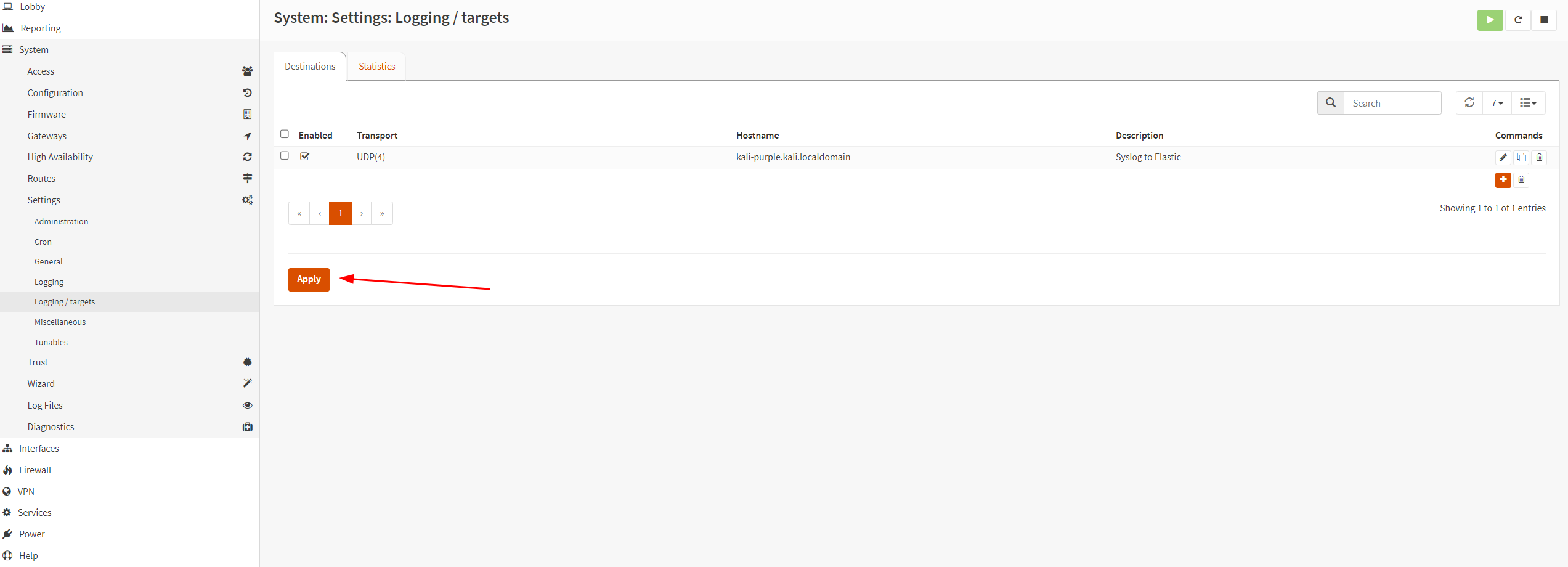
Elastic should now be ingesting the OPNsense logs.
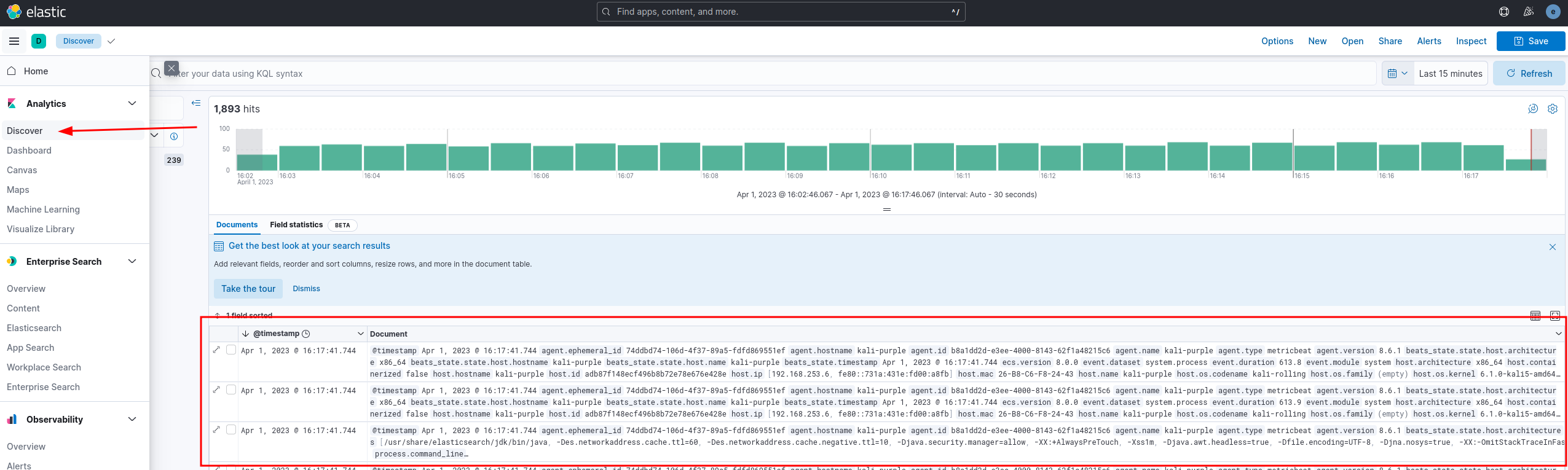
Installing Filebeat on OPNsense
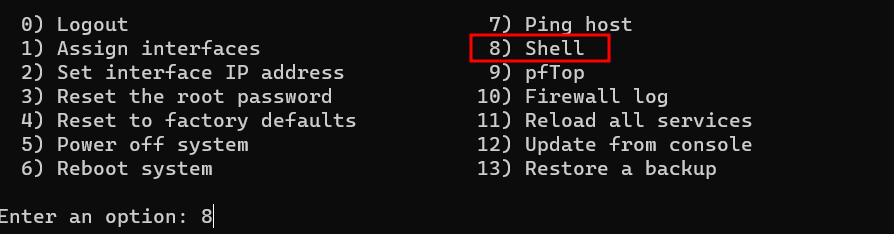
On OPNsense, login as root via SSH.
Select option 8 for shell.
cd /etc
mkdir pki
cd pki
mkdir rootIn a command line window on Kali Purple VM, enter the following command:
sudo su -
cd /etc/elasticsearch/certs
scp http_ca.crt [email protected]:/etc/pki/root/
Run the folowing commands on the OPNsense machine
opnsense-code ports
cd /usr/ports/sysutils/beats8
make install
If you want to use nano instead of vi, install with the following command:
pkg install nano
Edit the following config file
nano /usr/local/etc/beats/filebeat.yml
Add the following to the file:
output.elasticsearch:
# Array of hosts to connect to.
hosts: ["192.168.253.6:9200"]
# Protocol - either `http` (default) or `https`.
protocol: "https"
# List of root certificates for HTTPS server verifications
ssl.certificate_authorities: ["/etc/pki/root/http_ca.crt"]
# Authentication credentials - either API key or username/password.
#api_key: "id:api_key"
username: "elastic"
password: "your_password"
setup.kibana:
# Kibana Host
# Scheme and port can be left out and will be set to the default (http and 5601)
# In case you specify and additional path, the scheme is required: http://localhost:5601/path
# IPv6 addresses should always be defined as: https://[2001:db8::1]:5601
host: "https://192.168.253.6:5601"
ssl.verification_mode: noneSave and close.
Copy and paste the following:
cp /usr/local/share/examples/beats/filebeat.modules.d/suricata.yml.disabled /usr/local/etc/beats/filebeat.modules.d/cp /usr/local/share/examples/beats/filebeat.modules.d/system.yml.disabled /usr/local/etc/beats/filebeat.modules.d/cp /usr/local/share/examples/beats/filebeat.modules.d/nginx.yml.disabled /usr/local/etc/beats/filebeat.modules.d/cd /usr/local/etc/beats/
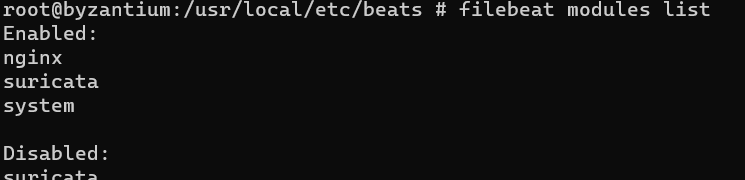
filebeat modules list
filebeat modules enable suricata nginx system
filebeat modules list
Should output the following
nano filebeat.modules.d/suricata.yml
Should show the following:
# Module: suricata
# Docs: https://www.elastic.co/guide/en/beats/filebeat/7.17/filebeat-module-suricata.html
- module: suricata
# All logs
eve:
enabled: true
# Set custom paths for the log files. If left empty,
# Filebeat will choose the paths depending on your OS.
#var.paths:filebeat test output -c /usr/local/etc/beats/filebeat.yml
filebeat test config -c /usr/local/etc/beats/filebeat.yml
filebeat setup -e
sysrc filebeat_enable="YES"
service filebeat start





