Kali Purple SOC: Part 9 – OpenCTI Installation and Setup

Installing OpenCTI
SSH into Kali Violet VM
Install dependencies
sudo apt update && sudo apt install curl -y
Install Docker
sudo apt install docker.io -y
sudo systemctl enable docker --now
Manage Docker as a non-root user
sudo usermod -aG docker $USER
chmod 666 /var/run/docker.sock
Install Portainer
docker volume create portainer_data
docker run -d -p 18000:18000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestCheck if the container has been started
docker ps
Login to Portainer
Login to Portainer at https://192.168.253.10:9443
Create username and password.
Click Get Started.
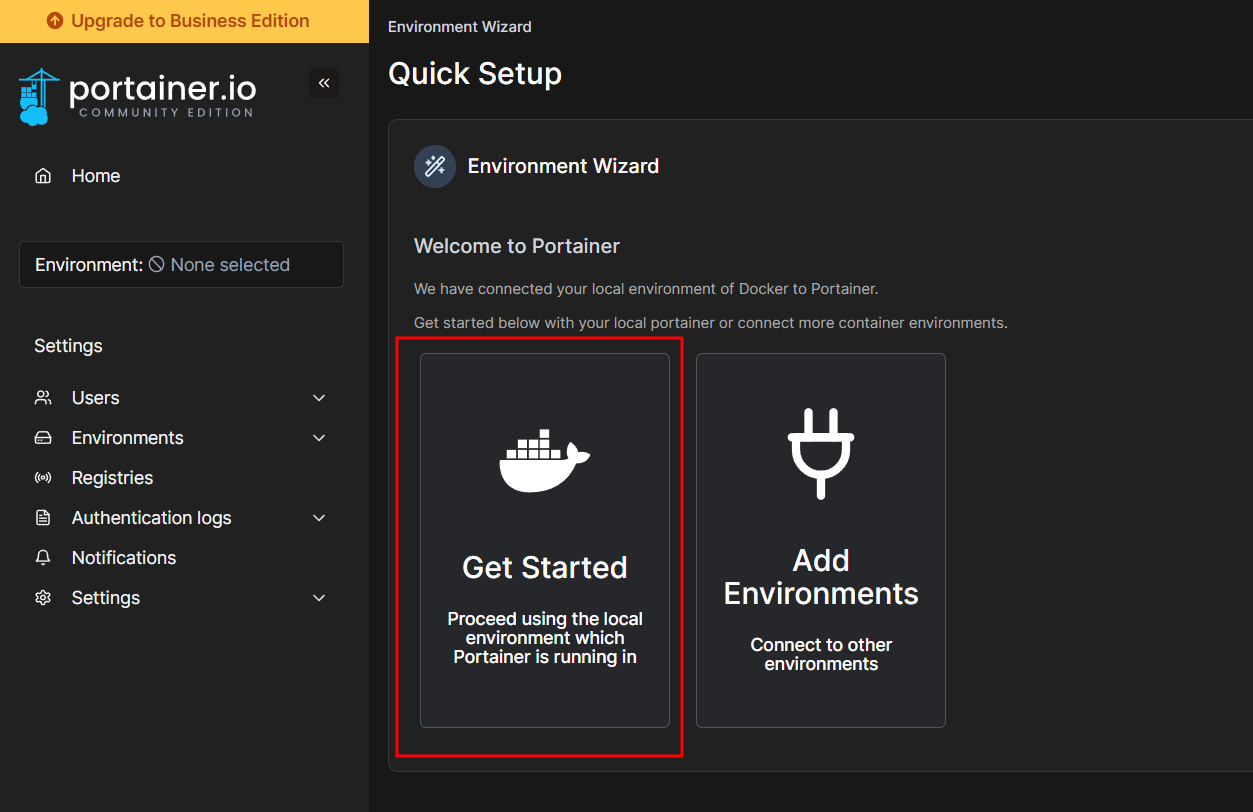
Click the local instance.
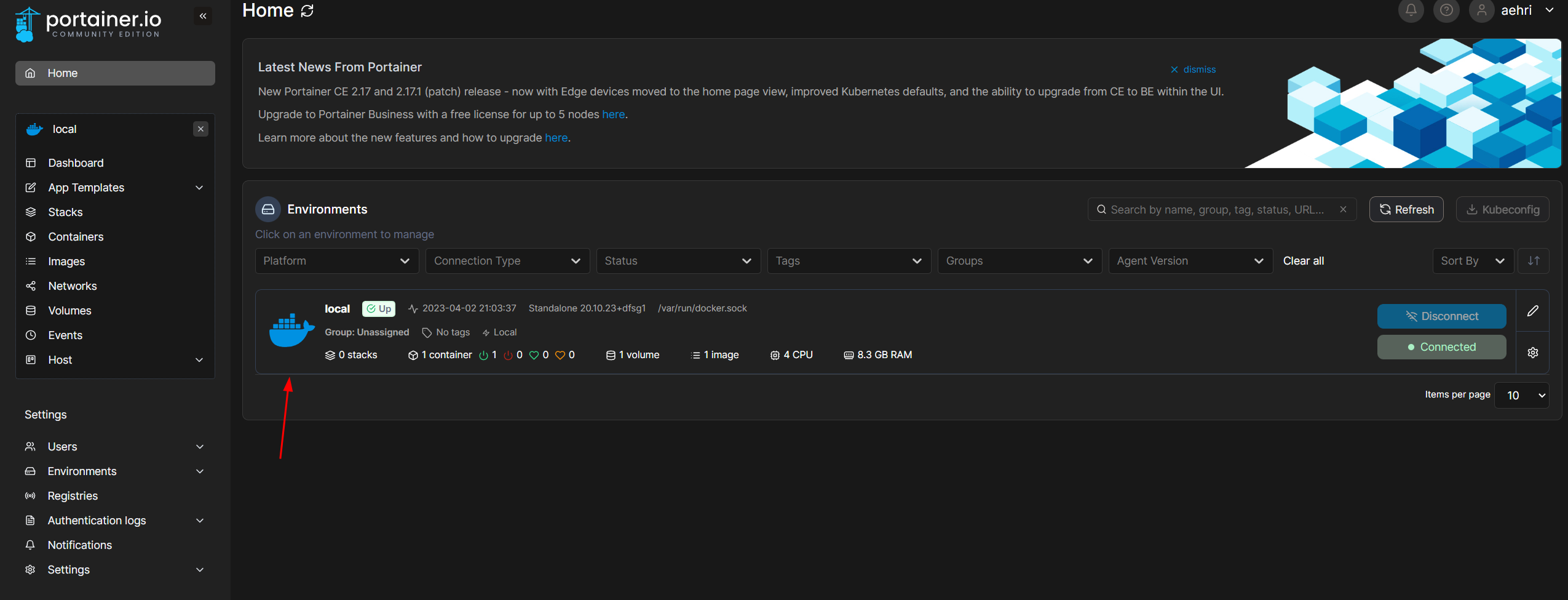
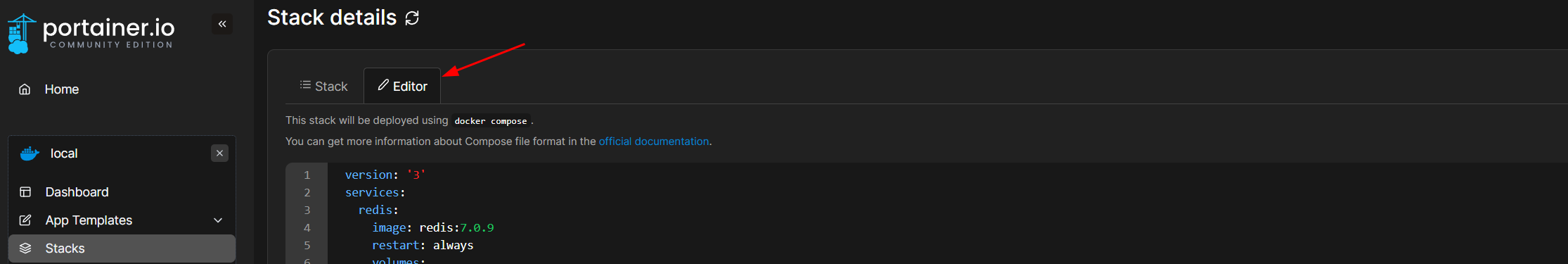
Click Stacks.
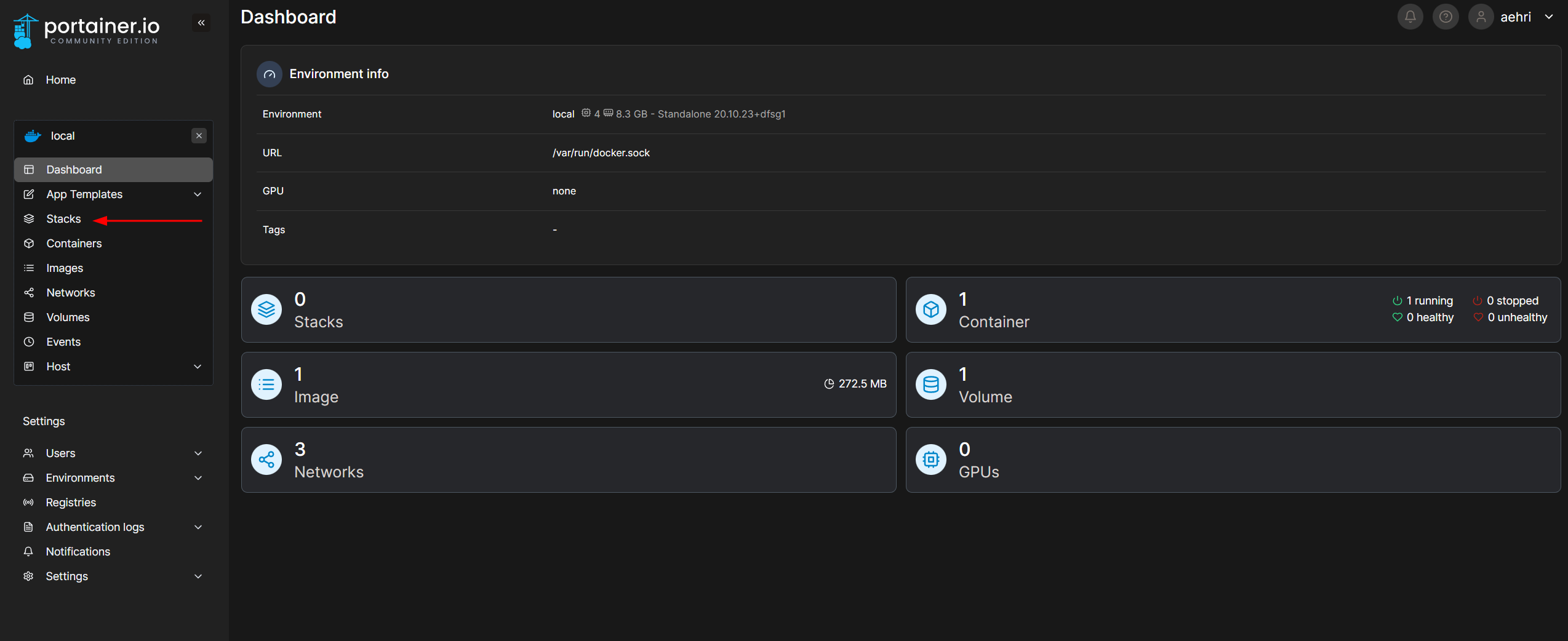
Add stack
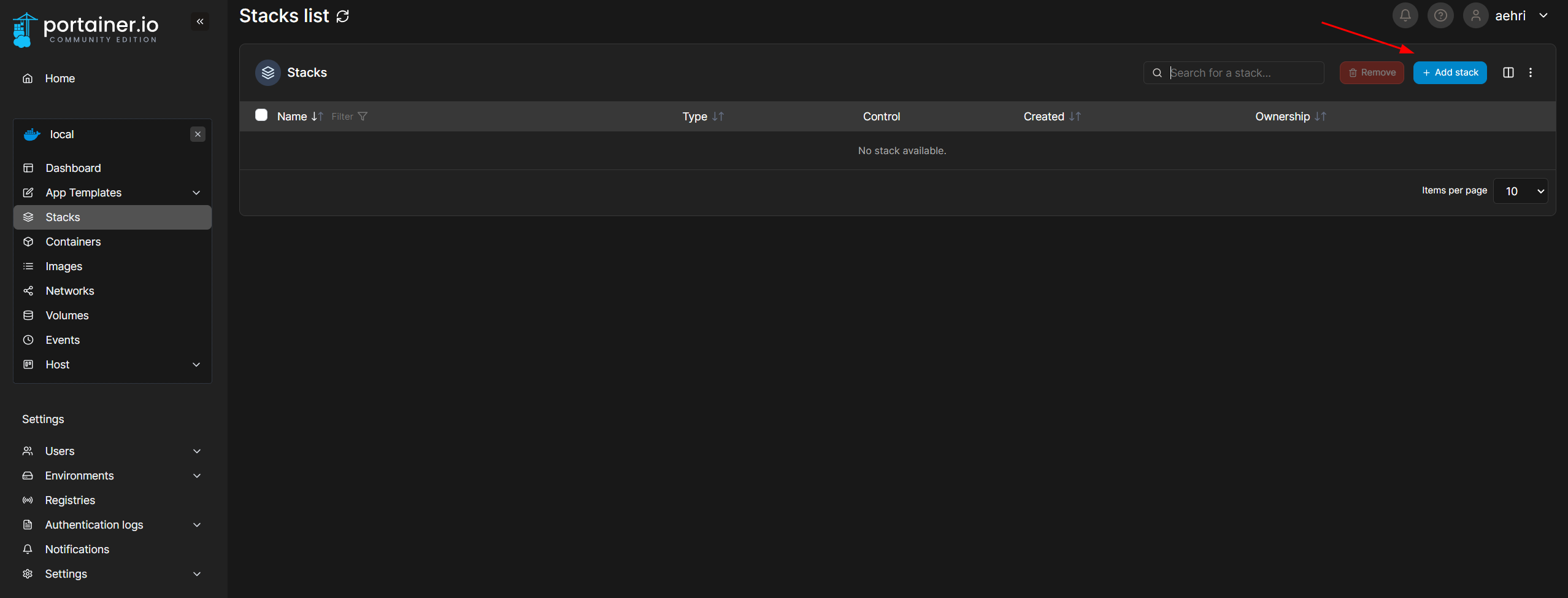
Open https://github.com/OpenCTI-Platform/docker/blob/master/docker-compose.yml and copy.
Name the stack opencti
Paste the code into the web editor.
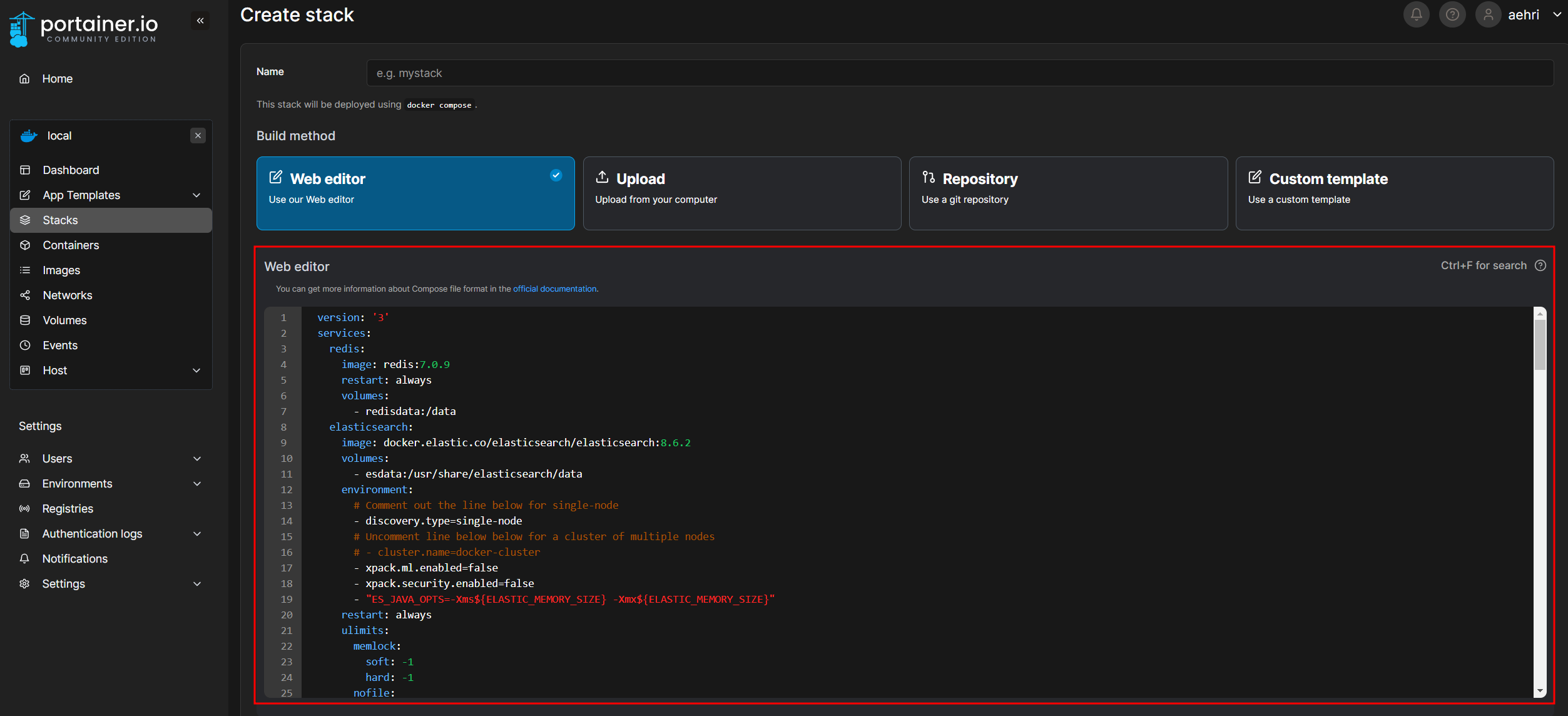
We need to create a number of environment variables before deploying the stack.
In a Kali Violet VM terminal window, run the following:
sudo mkdir /opt/opencti
cd /opt/opencti
sudo bash -c "(cat << EOF
[email protected]
OPENCTI_BASE_URL=http://192.168.253.10:8080
OPENCTI_ADMIN_PASSWORD=CHANGEMEPLEASE
OPENCTI_ADMIN_TOKEN=$(cat /proc/sys/kernel/random/uuid)
MINIO_ROOT_USER=$(cat /proc/sys/kernel/random/uuid)
MINIO_ROOT_PASSWORD=$(cat /proc/sys/kernel/random/uuid)
RABBITMQ_DEFAULT_USER=opencti
RABBITMQ_DEFAULT_PASS=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_HISTORY_ID=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_EXPORT_FILE_STIX_ID=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_EXPORT_FILE_CSV_ID=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_EXPORT_FILE_TXT_ID=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_IMPORT_DOCUMENT_ID=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_IMPORT_FILE_STIX_ID=$(cat /proc/sys/kernel/random/uuid)
CONNECTOR_IMPORT_REPORT_ID=$(cat /proc/sys/kernel/random/uuid)
SMTP_HOSTNAME=localhost
ELASTIC_MEMORY_SIZE=4G
EOF
) > .env"sudo chmod 600 .env
sudo cat .env
Copy the output of the sudo cat .env command and modify it to look something like this:
OPENCTI_ADMIN_EMAIL=your_email_address
OPENCTI_BASE_URL=http://192.168.253.10:8080
OPENCTI_ADMIN_PASSWORD=your_password
OPENCTI_ADMIN_TOKEN=8a9a6b15-48fa-48cb-a356-b2af79e44a4d
MINIO_ROOT_USER=a0a817ac-229a-43d6-b83e-f87573db56cc
MINIO_ROOT_PASSWORD=4c514035-5aea-4bd5-9b5e-4e2b96562c38
RABBITMQ_DEFAULT_USER=opencti
RABBITMQ_DEFAULT_PASS=f9a03fb5-b445-42f4-92eb-0ac0e8b01edc
CONNECTOR_HISTORY_ID=4edc8e23-147b-483c-ae5e-8512e39bb7d5
CONNECTOR_EXPORT_FILE_STIX_ID=655ccf74-461a-45fa-be7d-4494b0f4403b
CONNECTOR_EXPORT_FILE_CSV_ID=64ca4d7c-903f-4f16-921f-5620971adaab
CONNECTOR_EXPORT_FILE_TXT_ID=5c47adb1-291f-42ba-91b6-1b7f5b229f8f
CONNECTOR_IMPORT_DOCUMENT_ID=b3603efd-58a0-45ad-87b2-63c0ccd58444
CONNECTOR_IMPORT_FILE_STIX_ID=f23ccbea-31a6-4f61-bb7c-9b0cc5b7fda9
CONNECTOR_IMPORT_REPORT_ID=25ef4ec7-cc59-4da0-ad07-e2125ec8d5f6
SMTP_HOSTNAME=localhost
ELASTIC_MEMORY_SIZE=4GIn Portainer, click Advanced mode
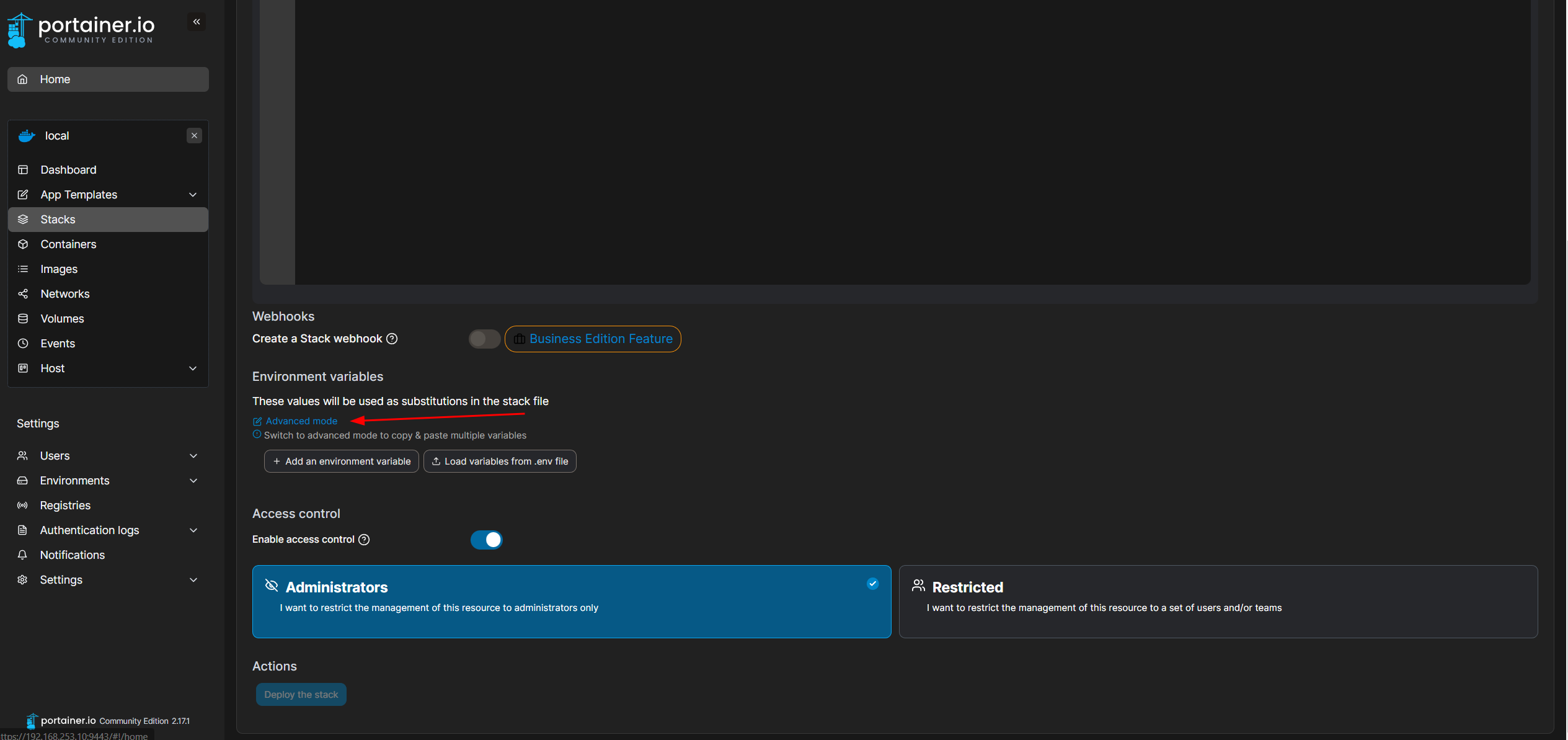
Paste the variables you modified in the field that appears.
Click Deploy stack.
After deployment is finished (will take several minutes to come up) login to http://192.168.253.10:8080
Enable HTTPS
In a terminal window on Kali Violet VM
sudo mkdir /etc/ssl/localcerts
openssl req -nodes -new -x509 -keyout server.key -out server.cert
Leave all blank (just hit enter through all of them)
sudo mv server.* /etc/ssl/localcerts
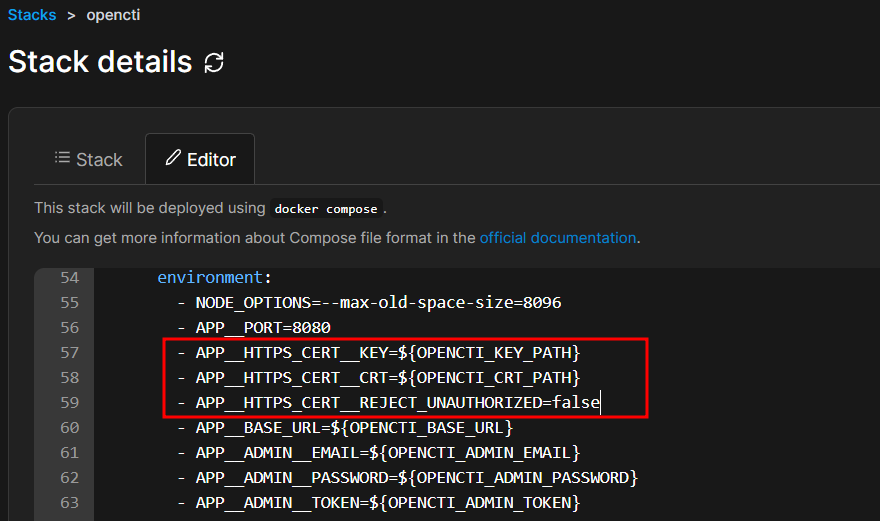
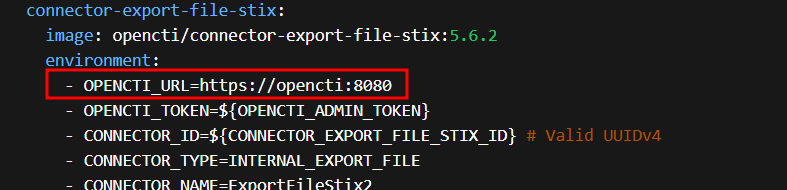
In the stack configuration, add the following lines to the "environment" section of the OpenCTI configuration:
- APP__HTTPS_CERT__KEY=${OPENCTI_KEY_PATH}
- APP__HTTPS_CERT__CRT=${OPENCTI_CRT_PATH}
- APP__HTTPS_CERT__REJECT_UNAUTHORIZED=false
To access the certificate and key, add the following volume section to the OpenCTI config as well:
volumes:
- /etc/ssl/localcerts/:/etc/ssl/localcerts:ro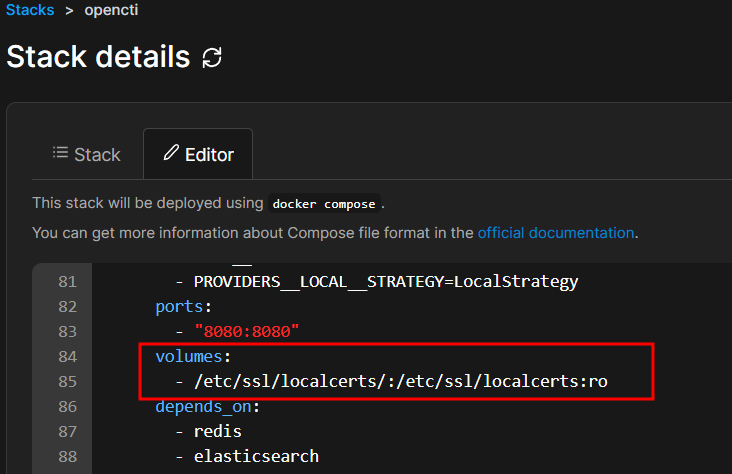
Assign the paths to the variable in the environment section:
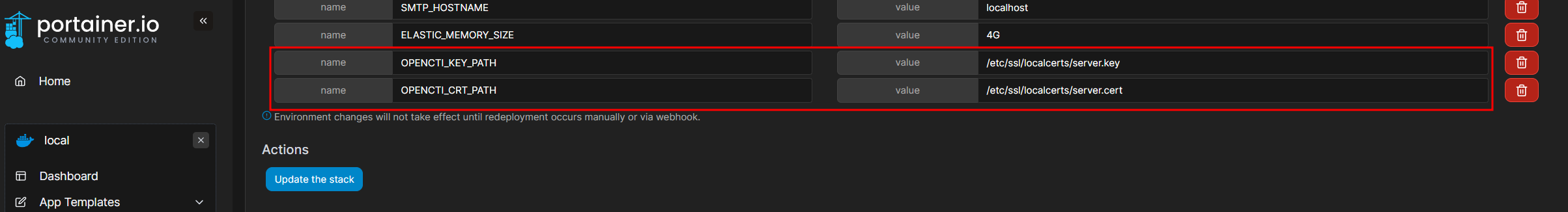
Replace all references to http with https
There should be 6 entries.
Update the stack.
Wait a few minutes, then logon to https://192.168.253.10:8080/
Add Connectors
Adding Connectors
Optional additional connectors not listed below can be found at https://github.com/OpenCTI-Platform/connectors/tree/master/external-import
OpenCTI Connector
Generate random UUID and append to the .env file from the command line.
sudo bash -c "(cat << EOF
CONNECTOR_OPENCTI_ID=$(cat /proc/sys/kernel/random/uuid)
EOF
) >> .env"sudo grep 'CONNECTOR_OPENCTI_ID' .env
Copy that into environment variables.
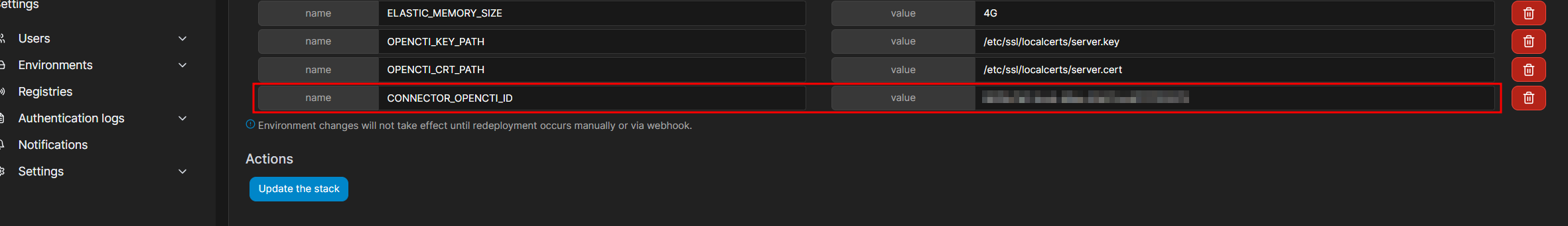
Add the OpenCTI connector
connector-opencti:
image: opencti/connector-opencti:5.5.2
environment:
- OPENCTI_URL=https://opencti:8080
- OPENCTI_TOKEN=${OPENCTI_ADMIN_TOKEN}
- CONNECTOR_ID=${CONNECTOR_OPENCTI_ID}
- CONNECTOR_TYPE=EXTERNAL_IMPORT
- CONNECTOR_NAME=OpenCTI
- CONNECTOR_SCOPE=marking-definition,identity,location
- CONNECTOR_CONFIDENCE_LEVEL=90 # From 0 (Unknown) to 100 (Fully trusted)
- CONNECTOR_UPDATE_EXISTING_DATA=true
- CONNECTOR_RUN_AND_TERMINATE=false
- CONNECTOR_LOG_LEVEL=info
- CONFIG_SECTORS_FILE_URL=https://raw.githubusercontent.com/OpenCTI-Platform/datasets/master/data/sectors.json
- CONFIG_GEOGRAPHY_FILE_URL=https://raw.githubusercontent.com/OpenCTI-Platform/datasets/master/data/geography.json
- CONFIG_INTERVAL=7 # In days, must be strictly greater than 1
restart: always
depends_on:
- opencti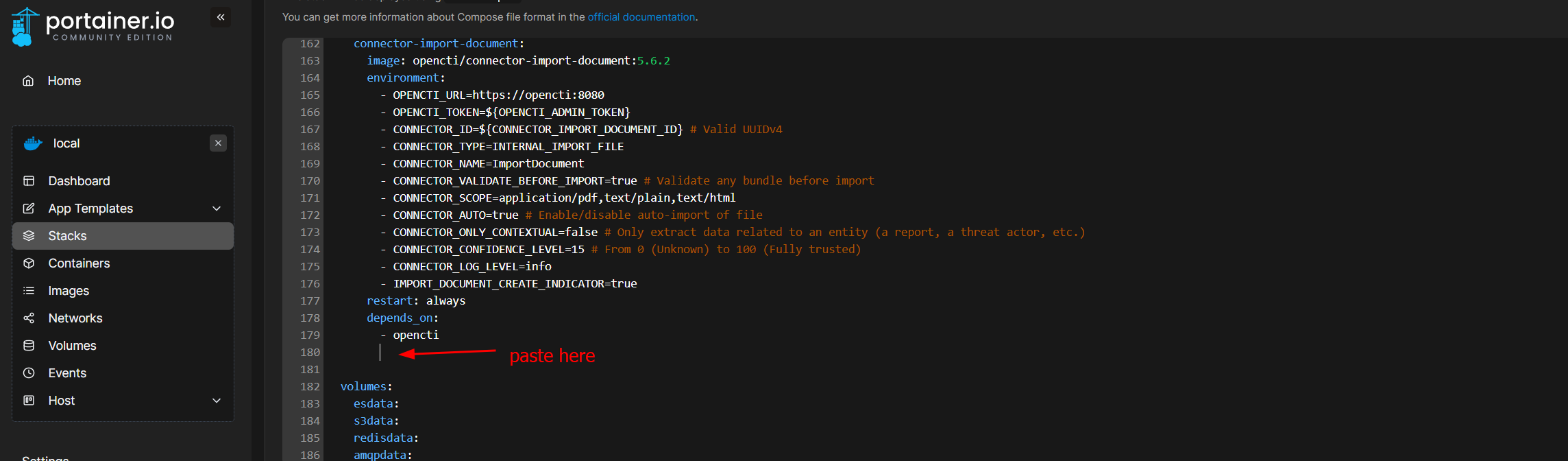
Deploy stack.
MITRE Connector
Generate random UUID and append to the .env file from the command line.
sudo bash -c "(cat << EOF
CONNECTOR_MITRE_ID=$(cat /proc/sys/kernel/random/uuid)
EOF
) >> .env"sudo grep 'CONNECTOR_MITRE_ID' .env
Copy that into environment variables.
Add the MITRE connector
connector-mitre:
image: opencti/connector-mitre:5.6.2
environment:
- OPENCTI_URL=https://opencti:8080
- OPENCTI_TOKEN=${OPENCTI_ADMIN_TOKEN}
- CONNECTOR_ID=${CONNECTOR_MITRE_ID}
- CONNECTOR_TYPE=EXTERNAL_IMPORT
- CONNECTOR_NAME=MITRE_Datasets
- CONNECTOR_SCOPE=tool,report,malware,identity,campaign,intrusion-set,attack-pattern,course-of-action,x-mitre-data-source,x-mitre-data-component,x-mitre-matrix,x-mitre-tactic,x-mitre-collection
- CONNECTOR_CONFIDENCE_LEVEL=75
- CONNECTOR_UPDATE_EXISTING_DATA=false
- CONNECTOR_RUN_AND_TERMINATE=false
- CONNECTOR_LOG_LEVEL=info
- MITRE_INTERVAL=7 # In days
restart: always
depends_on:
- opencti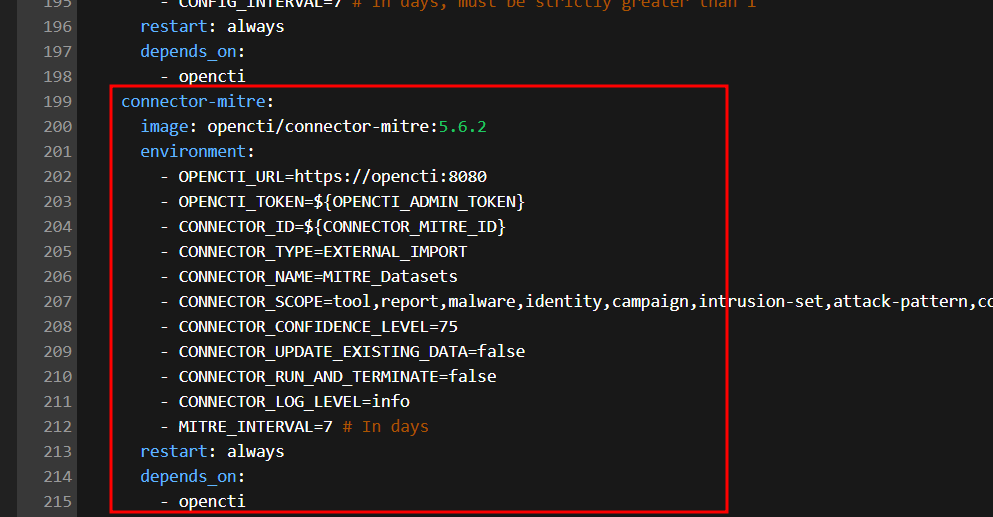
Deploy stack.
URLHAUS Connector
Generate random UUID and append to the .env file from the command line.
sudo bash -c "(cat << EOF
CONNECTOR_URLHAUS_ID=$(cat /proc/sys/kernel/random/uuid)
EOF
) >> .env"sudo grep 'CONNECTOR_URLHAUS_ID' .env
Copy that into environment variables.
Add the URLHAUS connector
connector-urlhaus:
image: opencti/connector-urlhaus:5.6.2
environment:
- OPENCTI_URL=https://opencti:8080
- OPENCTI_TOKEN=${OPENCTI_ADMIN_TOKEN}
- CONNECTOR_ID=${CONNECTOR_URLHAUS_ID}
- CONNECTOR_TYPE=EXTERNAL_IMPORT
- CONNECTOR_NAME=Abuse.ch_URLhaus
- CONNECTOR_SCOPE=urlhaus
- CONNECTOR_CONFIDENCE_LEVEL=40 # From 0 (Unknown) to 100 (Fully trusted)
- CONNECTOR_UPDATE_EXISTING_DATA=false
- CONNECTOR_LOG_LEVEL=info
- URLHAUS_CSV_URL=https://urlhaus.abuse.ch/downloads/csv_recent/
- URLHAUS_IMPORT_OFFLINE=true
- URLHAUS_CREATE_INDICATORS=true
- URLHAUS_THREATS_FROM_LABELS=true
- URLHAUS_INTERVAL=3 # In days, must be strictly greater than 1
restart: always
depends_on:
- opencti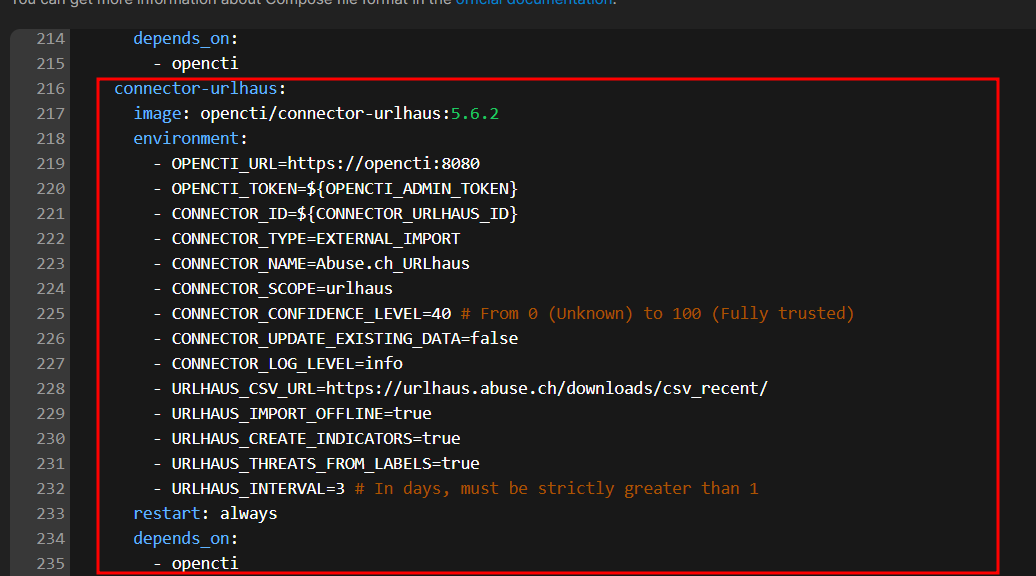
Deploy stack.
ABUSESSL Connector
Generate random UUID and append to the .env file from the command line.
sudo bash -c "(cat << EOF
CONNECTOR_ABUSESSL_ID=$(cat /proc/sys/kernel/random/uuid)
EOF
) >> .env"sudo grep 'CONNECTOR_ABUSESSL_ID' .env
Copy that into environment variables.
Add the ABUSESSL connector
connector-abuse-ssl:
image: opencti/connector-abuse-ssl:5.6.2
environment:
- OPENCTI_URL=https://opencti:8080
- OPENCTI_TOKEN=${OPENCTI_ADMIN_TOKEN}
- CONNECTOR_ID=${CONNECTOR_ABUSESSL_ID}
- CONNECTOR_TYPE=EXTERNAL_IMPORT
- CONNECTOR_NAME=Abuse.ch_SSL_Blacklist
- CONNECTOR_SCOPE=abusessl
- CONNECTOR_CONFIDENCE_LEVEL=70
- CONNECTOR_UPDATE_EXISTING_DATA=true
- CONNECTOR_LOG_LEVEL=info
- ABUSESSL_URL=https://sslbl.abuse.ch/blacklist/sslipblacklist.csv
- ABUSESSL_INTERVAL=10
restart: always
depends_on:
- opencti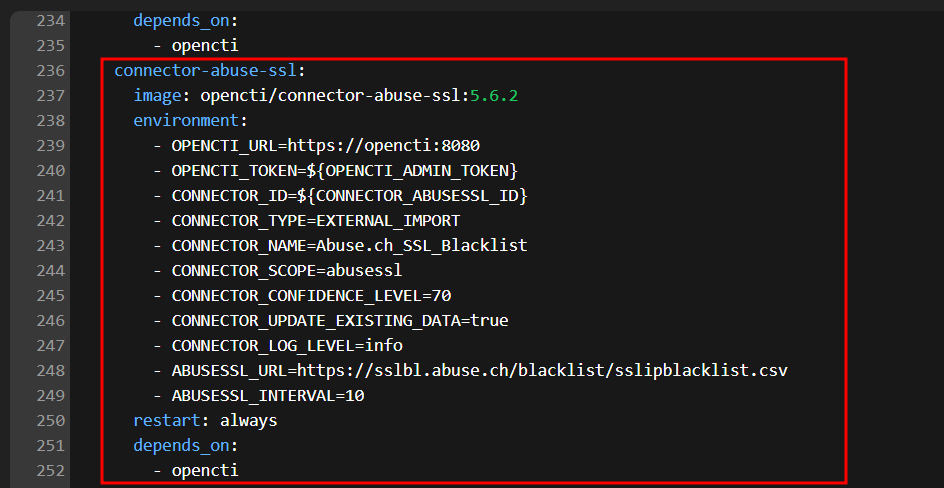
Deploy stack.
ALIENVAULT Connector
Go to https://otx.alienvault.com/ and register for a free account. Once logged in, go to Settings > Copy OTX key.
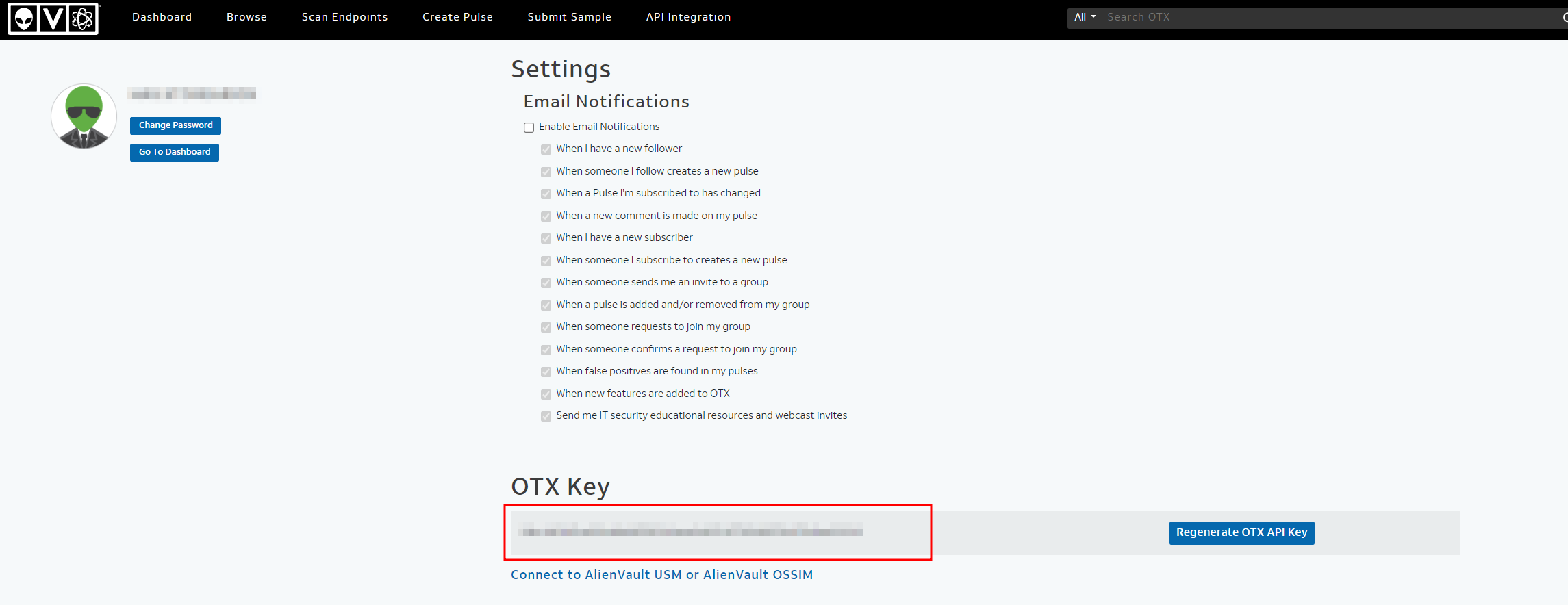
Generate random UUID and append to the .env file from the command line.
sudo bash -c "(cat << EOF
CONNECTOR_ALIENVAULT_ID=$(cat /proc/sys/kernel/random/uuid)
EOF
) >> .env"sudo grep 'CONNECTOR_ALIENVAULT_ID' .env
Copy that into environment variables.
Add the ALINEVAULT connector.
connector-alienvault:
image: opencti/connector-alienvault:5.6.2
environment:
- OPENCTI_URL=https://opencti:8080
- OPENCTI_TOKEN=${OPENCTI_ADMIN_TOKEN}
- CONNECTOR_ID=${CONNECTOR_ALIENVAULT_ID}
- CONNECTOR_TYPE=EXTERNAL_IMPORT
- CONNECTOR_NAME=AlienVault
- CONNECTOR_SCOPE=alienvault
- CONNECTOR_CONFIDENCE_LEVEL=15 # From 0 (Unknown) to 100 (Fully trusted)
- CONNECTOR_UPDATE_EXISTING_DATA=false
- CONNECTOR_LOG_LEVEL=info
- ALIENVAULT_BASE_URL=https://otx.alienvault.com
- ALIENVAULT_API_KEY=Enter_Your_API_Key_Here
- ALIENVAULT_TLP=White
- ALIENVAULT_CREATE_OBSERVABLES=true
- ALIENVAULT_CREATE_INDICATORS=true
- ALIENVAULT_PULSE_START_TIMESTAMP=2020-05-01T00:00:00 # BEWARE! Could be a lot of pulses!
- ALIENVAULT_REPORT_TYPE=threat-report
- ALIENVAULT_REPORT_STATUS=New
- ALIENVAULT_GUESS_MALWARE=false # Use tags to guess malware.
- ALIENVAULT_GUESS_CVE=false # Use tags to guess CVE.
- ALIENVAULT_EXCLUDED_PULSE_INDICATOR_TYPES=FileHash-MD5,FileHash-SHA1 # Excluded Pulse indicator types.
- ALIENVAULT_ENABLE_RELATIONSHIPS=true # Enable/Disable relationship creation between SDOs.
- ALIENVAULT_ENABLE_ATTACK_PATTERNS_INDICATES=true # Enable/Disable "indicates" relationships between indicators and attack patterns
- ALIENVAULT_INTERVAL_SEC=1800
restart: always
depends_on:
- opencti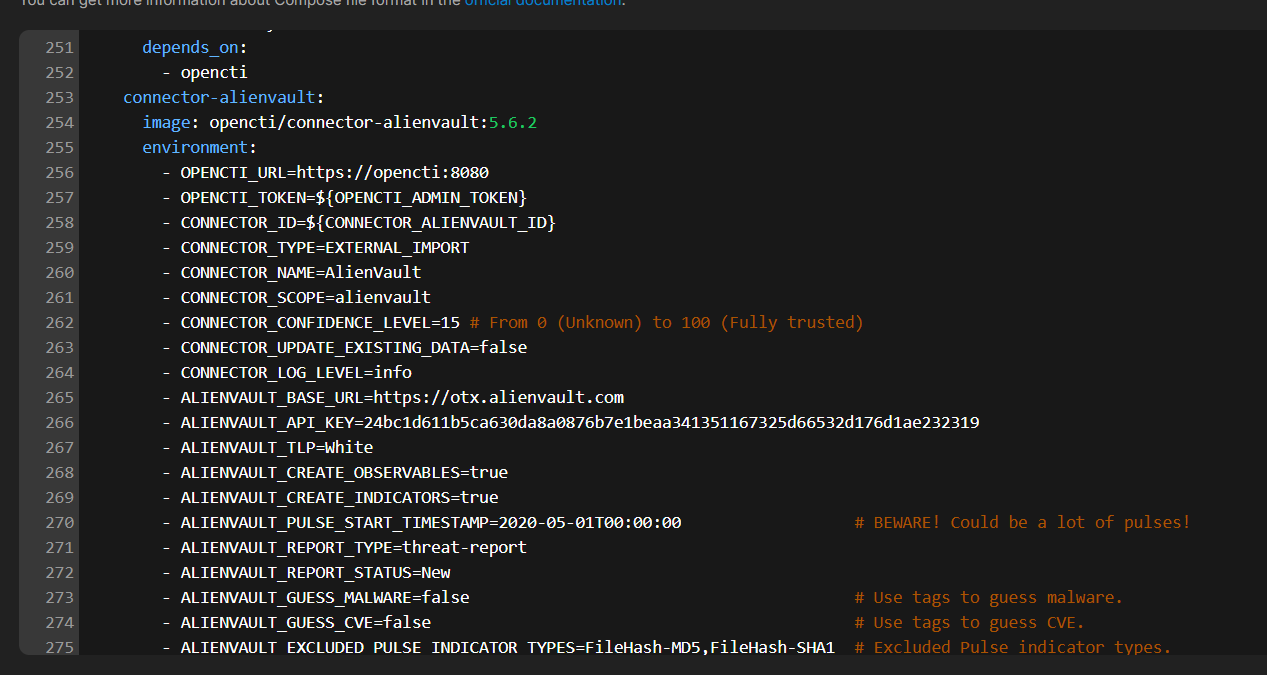
Deploy stack.





